

 |
 |
 |
|
|
|
|
|
|
|
|
|
 |
JonDonym, AN.ON and TorThe JonDonym / AN.ON technology is based on the principle of multiple (layered) encryption, distribution and processing. This procedure does not only protect your Internet activities from being observed by third parties (against your access provider, WLAN hackers, advertising services and websites), but also against observation by the individual JonDonym providers themselves. The anonymization service JonDonym is a development branch of the AN.ON Project. It consists of multiple user selectable mix cascades. A cascade consists of two or three separately encrypted mix servers. These mix servers are operated by independent and non interrelated organizations or private individuals who all publish their identity. The operators have to abide by strict provisions which prohibit saving connection data or exchanging such data with other operators.
Every connection from a user is differently encrypted for every mix server within a cascade and transferred through the cascade to the target, e.g. a website. Thereby no mix operator alone can by himself expose the user. Eavesdroppers on the connections to JonDonym cascades get garbage data only, as the connection to every mix is separately encrypted. Also, since a lot of users surf the anonymization service simultaneously, and thus share the same IP address, all connections of every user are concealed amidst each other: a correlation is not possible any more. 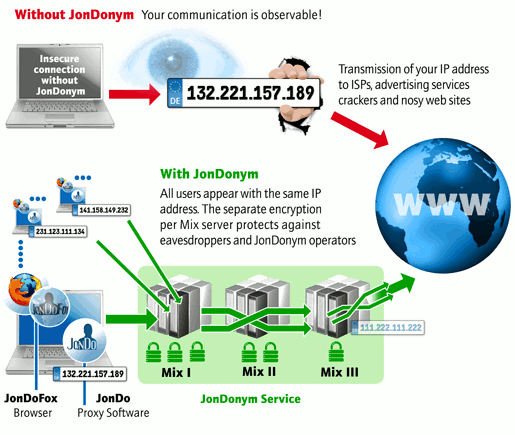 JonDonym has many advantages to other anonymization services:
Tor Oinion RouterA similar strong anonymization can only be offered by the non-commercial software Tor. Internet beginners should be careful with Tor. There is no control over who runs the Tor servers over which your private data travels. In the past, there has been ongoing suspicion that criminals and intelligence agencies exploit the Tor network in order to secretly attain information like passwords, bank accounts and credit cards. Researchers have shown in many cases how easy somebody can setup a spying Tor exit node:
Tor may be set as proxy in JonDo though, making surfing considerably slower but, in some individual cases, even more secure than with JonDonym alone. Like in Tor, the respective last mix server in a JonDonym cascade could record data which is not separately secured by HTTPS/SSL. Unlike Tor and other services, however, in JonDonym only certified and publicized persons and organizations may operate a mix server. The user may then decide for himself on whether he trusts the operator or not. If needed, they may simply choose other operators. All this makes it highly improbable for criminal operators to infiltrate JonDonym.
|
|
||||||||||||||||
|
|
|
|||||||||||||||||